Background – I’ve been working primarily in the cloud (IaaS and PaaS) for the past ten years, but for the last two, I’ve worked with security companies. As I ramped up and tried to learn the security market and key segments, I struggled to find a single point of view that reconciled the three core components of security (IMO): People, Process, and Technology. The NIST Cyber Security Framework 2.0 does a great job calling out the Process and People components. Still, in a rapidly evolving market, I couldn’t find what I call the IT Security Stack for companies that need to protect their data, employees, and customers from threats. We have the Cloud Stack (IaaS/PaaS/SaaS), the Web stack (LAMP), and the network stack (OSI), but the security stack eluded me.
This blog attempts to summarize and share my analysis and representation of the IT Security stack for most companies. The goal is to cover 80% of a customer’s security needs. I’m sure there are emerging technologies, threat surfaces, and companies I missed, but my intention is not an exhaustive list for the CyberSecurity professional, there are other infogrpahics that do that well. I’m focused on the business stakeholder who interacts with Security teams or is responsible for assessing their security risks and evaluating the investment in new technologies. If I missed something glaring, or if you have a relevant insight to share, I’d encourage you to comment below
The eight Security Categories in the Enterprise IT Security Stack.
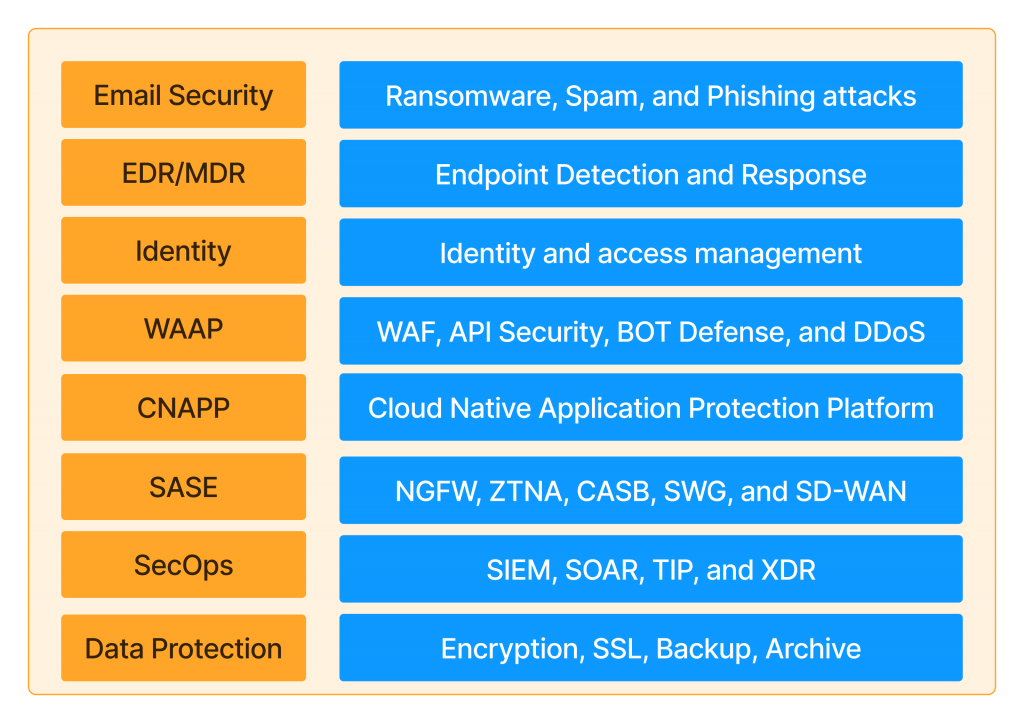
Some categories are made up of multiple security technologies. I tried to reference Gartner’s IT Glossary, MQs, and market reports for industry-accepted definitions. In the case of quickly evolving spaces such as CNAPP, I also cross-referenced analyst definitions with leading vendor websites and blogs. Definitions alone aren’t always helpful, so I put together the same chart with some questions stakeholders can ask themselves to determine whether they need such technology.
Questions to identify your need by Security Category
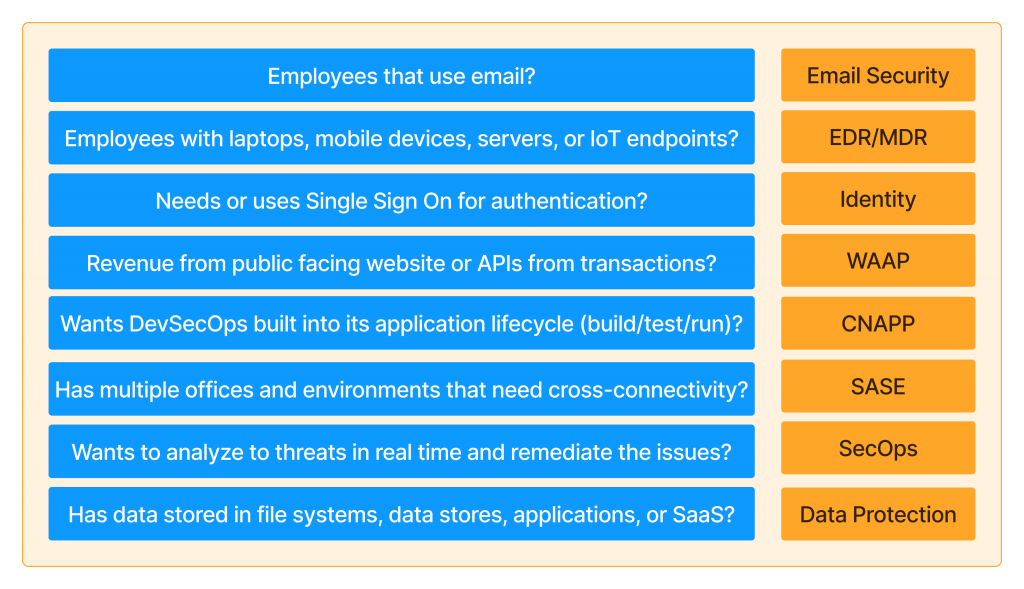
I also found that while the “IT Security Stack” and its category definitions were not well known among industry peers, most IT professionals were aware of companies in each space. Sometimes, you don’t know what you don’t know. The list below is representative but not exhaustive.
Representative security vendors by category
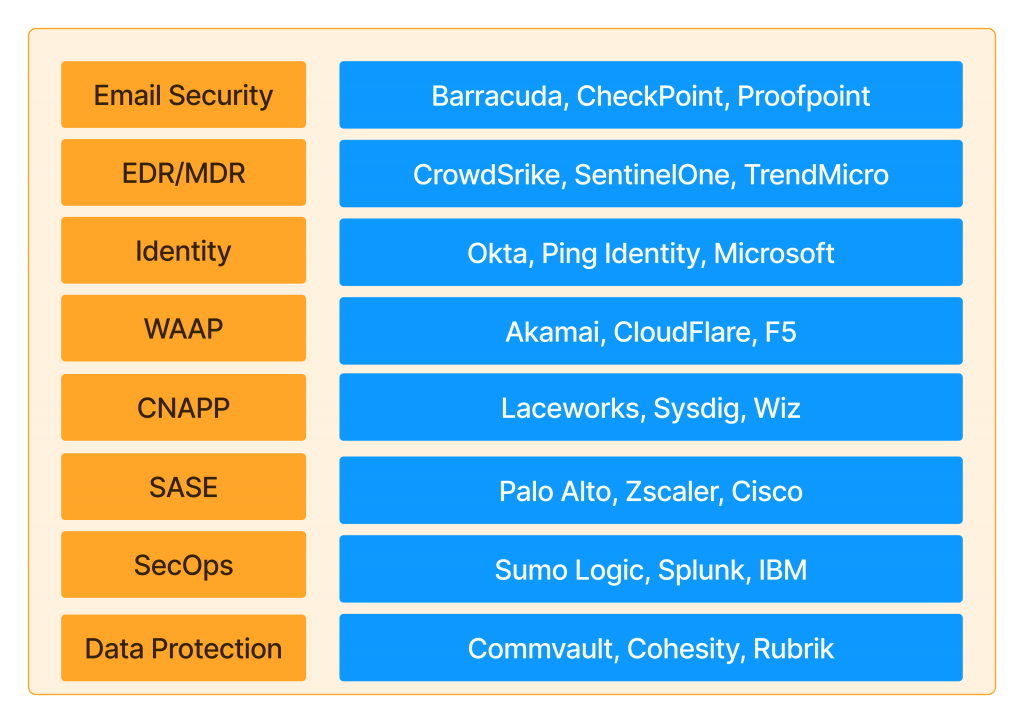
The eight Category definitions from industry analysts and leading vendors
- Email Security – This Forester Blog and The Enterprise Email Security Landscape, Q1 2023 report describes the email security categories excellently.
- EDR/MDR – The Endpoint Detection and Response Solutions (EDR) market is defined as solutions that record and store endpoint-system-level behaviors. A simplistic definition of managed detection and response (MDR) is that MDR is the managed version of EDR.
- IAM – Identity and Access Management (IAM) is a security and business discipline that includes multiple technologies and business processes to help the right people or machines to access the right assets at the right time for the right reasons, while keeping unauthorized access and fraud at bay.
- Web application and API protection (WAAP)– Typically delivered as a service, cloud WAAP is offered as a series of security modules that provide protection from a broad range of runtime attacks. It offers protection from the Top 10 web application security risks defined by the Open Web Application Security Project (OWASP) and automated threats, provides API security, and can detect and protect against multiple sophisticated Layer 7 attacks targeted at web applications. Cloud WAAP’s core features include web application firewall (WAF), bot management, distributed denial of service (DDoS) mitigation and API protection.
- CNAPP – Cloud-native application protection platforms (CNAPPs) are a unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production. CNAPPs consolidate a large number of previously siloed capabilities, including container scanning, cloud security posture management, infrastructure as code scanning, cloud infrastructure entitlement management, runtime cloud workload protection and runtime vulnerability/configuration scanning.
- SASE – Secure access service edge (SASE) delivers converged network and security as a service capabilities, including SD-WAN, SWG, CASB, NGFW and zero trust network access (ZTNA). SASE supports branch offices, remote workers, and on-premises secure access use cases. SASE is primarily delivered as a service and enables zero trust access based on the identity of the device or entity, combined with real-time context and security and compliance policies.
- SecOps (SIEM), (SOAR), and (XDR) – Crowdstrike has a great blog on XDR vs. SIEM vs. SOAR that I’d recommend you check out.
- Data Protection – Per the CISA, Cybersecurity is the art of protecting networks, devices, and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity, and availability of information. Data protection tools do this with a focus on data and can include solutions such as backup, archive, sister recovery, and encryption, to name a few.