I’ve been working for public cloud providers of IaaS and SaaS for over a decade, but I started focusing on security a little over a year ago due to some changes in my role. As with any new challenge, there is often a knowledge gap, followed by a steep learning curve and commensurate learning. If you are reading this, I’m sure you can relate to the experience of starting with a seemingly innocuous security question only to end up hours later feeling less informed than when you started because you now know how much you don’t know. In some attempt to compress years of knowledge into months, weeks, or even days, I would like to share one of these research experiences with you.
As I stumbled upon articles and blogs on security products such as ZTNA, WAFs, Secure Web Gateways, NGFWs, BOT Protection, DDoS, and SD-WAN, I found that most of these technologies fit into one of two buckets, Secure access service edge (SASE) or Web Application and API Protection (WAAP) as defined by Gartner. After trying to unwind the similarities, differences, and potential overlap of these two segments to be more effective in my daily role, I drafted this summary of my learnings. So without further ado, here are the primary differences between SASE and WAAP from a security neophyte.
TLDR version: WAAP focuses on protecting a public-facing application from security threats, and SASE focuses on enabling a company’s workforce to access internal applications and data from any location securely. (Corporate office, branch office, and remote employee)
Let’s start with a standard definition of WAAP and SASE from Gartner.
*What is Web application and API protection WAAP?*
Web application and API protection platforms (WAAPs) mitigate a broad range of runtime attacks, notably the Open Web Application Security Project (OWASP-F5 link) top 10 for web application threats, automated threats, and specialized attacks on APIs. WAAP comprises a suite of tools that includes next-generation WAF, API security, advanced bot protection, and DDoS protection. Definition – Gartner
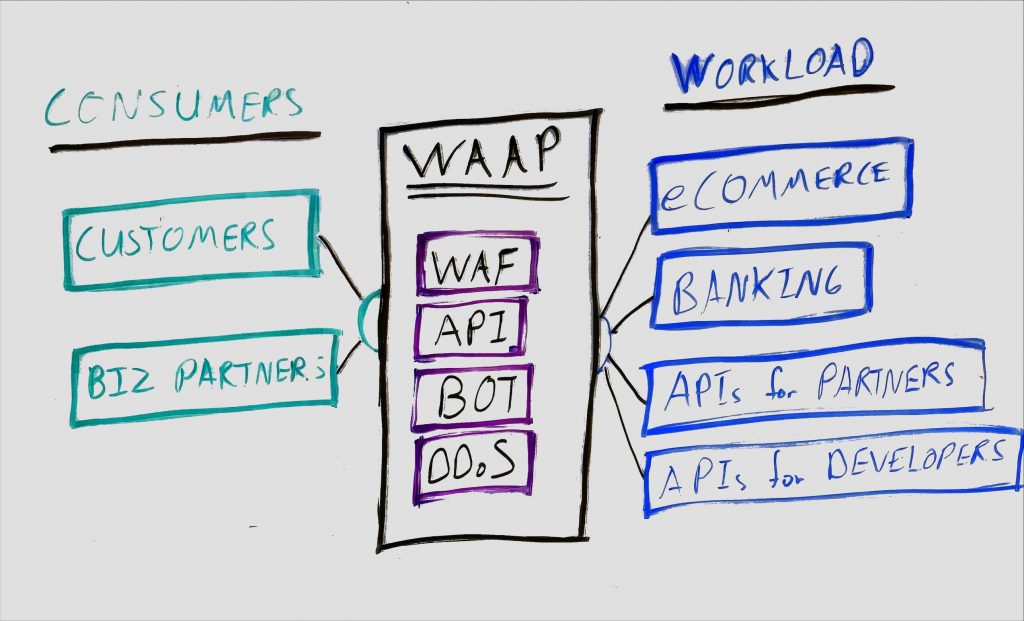
What kind of deployment options exist for WAAP?
The web application and API protection solutions can be deployed as WAAP services (SaaS) or as WAAP (Virtual or Physical) appliances. Cloud WAAPs are cloud-delivered services that primarily protect public-facing web applications and APIs. Definition – Gartner
What is Secure access service edge (SASE)?
Per Gartner, Secure access service edge (SASE) delivers converged network and security as a service capability, including SD-WAN, Security Web Gateway (SWG), Cloud access security brokers (CASB), next-generation firewall (NGFW) and zero trust network access (ZTNA). SASE is primarily delivered as a service and enables zero trust access based on the identity of the device or entity, combined with real-time context and security and compliance policies. SASE supports branch offices, remote work, and on-prem secure access use cases. Gartner forecasts that the SASE market will grow at a CAGR of 32%, reaching almost $15 billion by 2025.
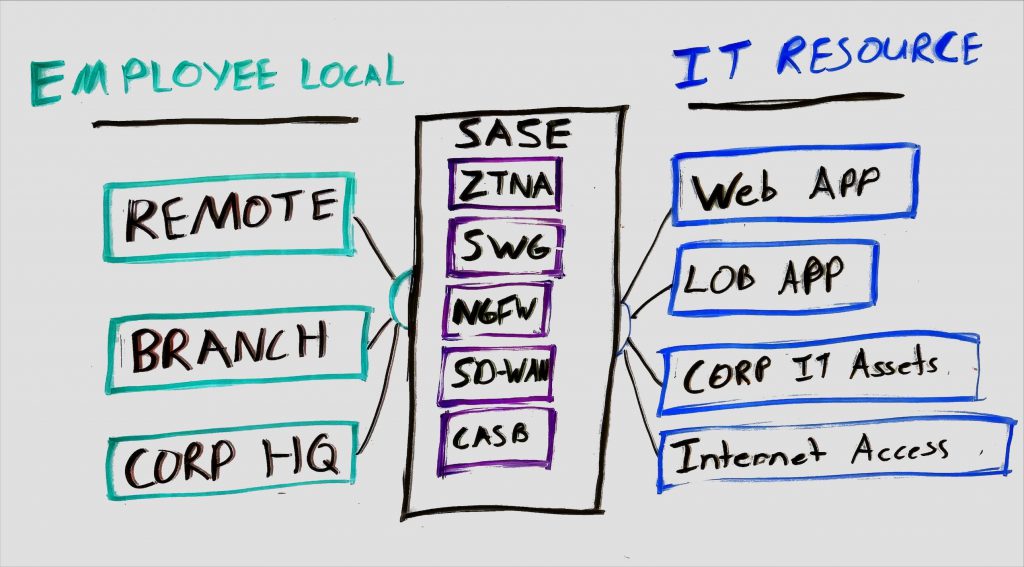
How does WAAP differ from SASE?
SASE’s primary goal is to enable and secure anywhere, anytime access, network, and network security for a company’s workforce to protect internal networks and data. WAAP solutions protect a company’s public-facing applications from external threats. Today I’ve found that the current SASE and WAAP offerings contain these core technologies.
SASE Products
- SD-WAN
- Security Web Gateway (SWG)
- Cloud access security brokers (CASB)
- next-generation firewall (NGFW)
- zero trust network access (ZTNA)
WAAP Products
- Web application firewall
- API protection
- Bot Detection
- DDoS
Some might argue that SASE encapsulates WAAP, but I don’t find that very helpful and prefer to cite the distinct technologies to avoid peanut-buttering buzzwords enabling you, the individual, to discern relevance.
There are areas of overlap in functionality and integration, but the above mental models helped me differentiate each segment’s customer use cases and target personas.
Full disclosure, this explanation is an attempt to help others save hours on a question I struggled to find a succinct answer for. There are plenty of resources to dive deep into the technologies that make up these security domains, as well as a storied history of the evolution of the networking and security market.